Answers to discussion topic questions in Unit 7
Please make sure you understand the answers before you attempt the practice
quiz or unit test. Many of these answers came from your fellow students.
- Explain how a vacuum tube can act as a switching device.
In its simplest form, a vacuum tube consists of a
filament and a plate in a hard vacuum. The filament (cathode) is the
source of electrons and is similar to the filaments found in an incandescent
light bulb. When heated, electrons "boil" off the surface.
The plate (anode) can establish the flow of current if it is given a positive
charge with respect to the filament. That is, if the
plate holds a positive charge, electrons flow from the filament to the
plate. Thus, the plate can switch on or off a flow of current. In
an improvement, another electrode called the "grid" (a bent wire or screen)
was placed between the filament and plate. This grid would act to control
the current flow between filament and plate. For example, if the grid
has a positive charge, it would promote the flow of electrons to the plate
(because this would promote electron motion away from the filament).
However, if the grid was charged negatively (with respect to the filament), it
would repel electrons and dampen the filament/plate current. Perhaps you
can see how this vacuum tube acts as an ampler (as well as a switch). The plate serves as
the signal output. Any varying signal on the grid is
matched by a similar (but larger) signal on the plate.
All computers require some routine maintenance. Offer ONE piece of advice
you should follow to ensure that your computer will keep working, run with
optimal performance, or avoid potential problems. Please avoid
posts dealing with intruder prevention (like virus protection) or avoiding SPAM
which are covered in other topics (the Internet). That is, limit the
post to keeping the hardware healthy.
Back up all important data often (and keep a copy off your premises)
Use the system maintenance programs such as disk defragmenter (defrag), disk clean up,
and system restore (make a restore point when your computer is healthy)
Dust can build up and block air flow around your CPU heat sink. Keep this
area clean.
Protect your system with a surge protector and unplug the computer during
intense lightning storms.
Never shake, rattle, or roll your computer when the hard drive is accessing data.
The read/write heads can touch and damage the disk.
Hardware
- 1. Moore's Law is a rule of thumb related to advancements in chip design.
What is this "law" and how well has it held up?
Way back in 1965, Gordon Moore predicted the number of
transistors would double every 2 years (he originally predicted every year).
This prediction held up remarkably well. Every
18 months the number of
transistors on a chip have doubled. However, in a
2007 article, Moore
predicted that this exponential growth would only last for another 15 years.
In 2015, Intel announced definitely the numbers to show that progress truly
was slowing down. In the same year, Gordon Moore himself stated that he saw
his Law dying within the decade. Advances in nanotechnology may help increase
the rate again, but for now we are sitting at roughly 3 years per component
doubling.
- 2. What is virtual memory? Under what circumstances is it used?
When conventional memory resources become tasked, the
computer will use the hard drive as a last resort. Access time to the
hard drive is significantly slower than convention memory but in a pinch, the
hard drive will serve as virtual memory for data with the lowest priority.
- 3. Compare the best chips on the market by Intel and AMD. What is the
target audience for these chips? That is, why would someone really need this
chip?
Since new chips come flying off the assembly line, it is
easiest to provide these links:
Intel press releases and
AMD press releases
These chips use dual and quad processors on the same die. However, this
kind of speed is only required for PC gamers and video rendering. If you
are like most folks who use their computer for email, writing letters, and web
surfing ... these new chips are a waste of your money. For example, I
could easily do
most of my work for this class on a slow, ancient Pentium class processor. I use
my faster (Core-2) notebook for video production.
- 4. Find an independent source that compares CPU sales from Intel vs. AMD. Is
the gap changing with time?
This
graph says it all. Prior to 2006, things were looking good for AMD
but after that .... Intel took the bull by the horns. Intel's market
lead is around 75% (which fluctuates from year to year but not by much). The
gap narrowed slightly in 2018 with huge
AMD sales.
Note: Smart phones are now so popular that companies like Qualcomm,
Samsung, and Apple are making big headway in the CPU market. Taking this
into account, AMD has slipped down the list quite a bit.
Software
- 1. What is the advantage of using drivers (software which
tells the OS how to handle hardware)?
When you purchase a computer peripheral (printer,
scanner, etc), you usually have an install disk that loads drivers
for that equipment. In the "old days" (mid 80's), folks who wrote
software had to worry about how that software would interact with systems that
ran it. They wrote software called "embedded drivers" which were part of
the main program. So if you ran Lotus 123 (for example), the Lotus
program had to know how to handle every kind of printer on the market.
This was a very bad design because new printers hit the market and also
because each software application had to spend lots of time and money making
sure their software would print correctly. To get around this problem,
Microsoft Windows offered a way for software to interact with hardware using
drivers. These programs must meet Windows communication standards.
This got software writers off the hook because they were no longer responsible
for that aspect of their product. In addition, any software application
could use the same driver to run the peripheral (printer). Perhaps the best part of
this design is its adaptability. If there is a bug in the program, you
can simply download an updated driver.
- 2. Why wasn't Gary Kildall the richest person on the planet? Give a one
paragraph overview of his missed opportunity. In your answer, explain the
role Tim Paterson had in the story.
When IBM wanted to introduce a PC (in the early 80's),
they needed an operating system. They went to Bill Gates who referred
them to Gary Kildall. Gary Kildall had just what IBM was looking for ...
an OS which looked like DOS. IBM tried to work a deal with him but found
him very rude. They went back to Bill Gates and he purchased a program
written by Tim Paterson for $50,000. This program was basically a
rip-off of Gary Kildall's program - DOS. Gates took this to IBM and it
became the OS for their PC. The rest is history.
- 3. Sometimes software is so popular it compels people to buy computer systems
just to use it. What was the first of the "killer apps" (for killer
applications) that hit the PC market? Hint: The two people who wrote it did
not patent the idea so someone else made a fortune under a different product
name.
VisiCalc
was the first "killer app". This was a spreadsheet program used by
accountants and marketers for forecasting. Since Dan Bricklin and Bob
Frankston (the two authors) did not patent their idea, companies like Lotus
123 (and later MS Excel) made fortunes on the idea.
- 4. What is "plug and play"? How does the OS know how to run hardware with
this tag?
When you insert any device into your USB port (or some
other bus), you would like it to work without having to load software or
manually allocate system resources. I remember purchasing peripherals
(modems and such ) and loading software and moving jumper pins or flipping DIP
switches ... and becoming very frustrated trying to make everything work
properly.
There had to be a better way! This is what "plug and play" is designed to do. Let's suppose you just
plugged a new flash memory card into your USB port. How does your OS
recognize it? It all gets done with help from the Windows BIOS
chip (known as the PnP Bios). This sends out signals to all peripheral
bus routes. If something is plugged in, it requests some information
from that device. Each "plug and play" device has a chip with software
encoded on it called an ID string which gets sent to the Windows PnP BIOS.
The manufacturer of the device has to make sure that the OS has the
appropriate driver stored on the hard drive. The OS then automatically
configures the necessary drivers (or asks for a disk if it can't find any)
... which then arranges lines of communications (bus resources) for that
device. This lets the OS know what the device is and how to talk to it.
Storing Data
HDD vs. Flash Memory (and SSD) : Compare hard drive data storage against flash
memory in terms of cost per MB and access time.
HDDs are slower than SDDs. SDD typically have
read/write speeds in the 500 MB/s range. A typical Hard drive have average
read speed of 128 MB/s and a write speed of 120 MB/s. However, while HDDs are
slower, they are cheaper, too. The cost is about $.03 per gigabyte versus an
average $.20 per gigabyte for SSDs. (2018
source)
Another consideration is how long you can expect the device to last. Flash storage will typically wear out after
100,000 write
cycles. Special file systems or firmware designs can mitigate this
problem by spreading writes over the entire device, rather than rewriting files
in place. On the other hand, hard drives fail for a large number of
reasons ... mainly because they have moving parts which can be damaged or wear
out. One
study
of 100,000 hard drives showed 1.7% died within the first year and 8.6% bit the
dust within 3 years.
Future Optical storage devices?
A Magneto-Optical disks have been around for some time
but mostly in Japan. This technology uses a laser (instead of a read/write
head) to change the magnetic state of a disk (like a standard hard disk).
A technology known as UDO (Ultra Density Optical) is a
twist to current CD techniques. This uses a blue laser to make a
phase change to a crystalline material on a disk. The blue light means you
can place more data in a smaller space (like Blu-Ray). This allows 60 GB
of storage per disk. Just like CD's come in write once and re-writable
formats, so, too, does UDO. More
here.
Multilayer Approaches:
Background: One of the reasons why there are only
two layers of data on standard DVD's is the fact that you have to read through
the top layer to get to the next one. This creates "noise" and scattering
that can interfere with accuracy. If you were to add a third layer, the
build up of noise would cause read/write errors. The following
technologies are attempts to solve this problem.
Fujifilm plans on introducing a 1 TB disk in 2015 which
has 8 layers of recorded data. They use a "two-photon absorption method"
which uses two photons of light to generate heat in a very small area.
Read more
here.
Digital Multilayer Disk (DMD)
- formerly called Fluorescent Multilayer Discs (FMD) - Instead of being
limited to just two layers (due to interference, scattering, etc.) on
conventional optical disks, the use of fluorescence may allow for up to 100
recording layers. Russian scientists have found materials which exhibit
fluorescent properties when excited by a (red) laser of a certain intensity. Once it obtains these
properties (becomes a "1"), the laser reads the data by exciting the material to
emit a unique color. A disk can hold 20 GB of data with the prospect of up
to 100 GB.
A company named Mempile is in the process of
developing a new kind of disc that can have up to 200 virtual layers! The
reason this is possible is that the disc is made of a mixture of materials and
its called ePPMA. The disc is a see-through yellow which is a very important
aspect which allows the many layers to be read. Reading and writing is done
when laser light (of various intensities) produces photochemical changes to
the disk itself. They hope to put over 1 Terabyte on a single disk.
Links
here and
here.
Holographic Data Storage
- It should be obvious that a hologram can store data. The neat thing
about this idea is you can stack multiple layers together and still access the
data on each layer. This makes holographic storage a 3 dimensional medium,
- capable of storing a great deal of data in a small volume. We are talking
about terabytes per disk!!!
Multiplexed Optical Data Storage (MODS) may be able to
store 100-200 bits of information on a single pit. The key is to use
polarized laser light. This is accomplished by making the storage
medium sensitive to polarized light. Read more
here.
Another MODS approach is to design disks with
asymmetric pits. Using current technology a pit is just a pit. This
approach uses pits at 332 different angles which reflects the laser to different
angles. This encodes different information for each angle. This
encoding of information could fit a Terabyte of memory on a single disk.
Read more
here.
Super-RENS
(Super REsolution Near field Structure) - In an effort to reduce the physical
size of the data bit on an optical disk, it was found that you can obtain
resolutions which are beyond the current limits of the industry standards (blu
ray). A hemispherical lens is placed just over the recording layer which
helps focus the laser beam to an even smaller area, providing a "super
resolution" which, apparently, has yet to be understood by the comments
in
this article.
OK .. this isn't optical but sure needs to be added because it is
soooooooo cool
Storing data on DNA.
Harvard researchers are able to store 5.5 petabits (700 terabytes) of data on a
single gram of DNA. How it works. “ the researchers first translated written
words or other data into a standard binary code of 0s and 1s, and then converted
this to a trinary code of 0s, 1s, and 2s…… The researchers then rewrote that
data as strings of DNA’s chemical bases: As, Gs, Cs, and Ts. At the storage
density achieved, a single gram of DNA would hold 2.2 million gigabits of
information, or about what you can store in 468,000 DVDs. What’s more, the
researchers also added an error correction scheme, encoding the information
multiple times, among other tricks, to ensure that it could be read back with
100% accuracy”. “Researchers claim the data could last over 10,000 years and can
be read by anyone so long as they have access to a machine that can read DNA”.
Now we can’t run out and purchase DNA drives right now, the technology needs to
be standardized and the cost of $12,400 per megabyte is a bit cost prohibitive
for mass use. Researchers hope with advances to the field and private companies
developing cost effective options we may see the first DNA data storage devices
in our lifetime.
... on the same topic
Professor V Renugopalakrishnan has claimed to develop a
layer of protein that is made of genetically altered micro proteins that
are able to store data . It is light activated and can store about 50
terabytes. It captures and stores sunlight to convert it to chemical energy.
These disks will be able to hold 20 times more than Blue-Ray disks and predicted
to hold about 50 terabytes.
http://www.technotactics.in/protein-coated-disk-an-evolution/
Computer Memory
- 1. What was the Y2K problem? In your answer explain what caused it. Hint:
It had something to do with the subject of this page.
Early programmers abbreviated the year to two digits.
That is, the year 1963 was shortened to 63. The problem was, when the
century moved from 1999 to 2000 the computers would think the time was moved
back to 1900. Besides the inconvenience, it was thought that programs
might crash as a result. Programmers spent years trying to correct this
problem but there was real apprehension that airplanes would crash when the
time hit. Note: I was on an airplane at the time and I remembering
ordering a $5 beer ... just in case. LAX was a ghost town when we
landed. Why was this allowed to happen? In the early days RAM was
so expensive that it was felt that you could conserve valuable resources by
taking this short cut.
- 2. Cache memory is subdivided into L1 and L2. What is the primary difference
between these two classifications?
L1 is known as primary cache memory and is printed
directly on the CPU. Only the most frequently used and most important
data is stored there (which is the most expensive real estate on the CPU).
The close physical proximity to the CPU becomes important because access to
the CPU is restricted by the speed of light (which is fast but not infinite).
L2 cache (secondary cache) has a slightly lower priority and is located close
to but not necessarily on the CPU itself (but may be printed on the CPU as
well). L2 cache memory is typically larger but slower than L1 cache
memory.
Cache memory is expensive but fast. This form (SRAM) uses 4 transistors
to store a bit and 2 more transistors - one each for reading and writing.
It is volatile (meaning it goes to zero if the power is lost).
Are there any intriguing technologies that may replace conventional dynamic
or static RAM? You bet there is! Any of the ideas below could be the
future of computer memory.
3D XPoint - Intel and Micron have
introduced a new type of non-volatile memory known as 3D XPoint (Cross Point).
The developers are very tight lipped about how it works but it does not
use transistors and likely involves a phase change of a substance. Each
phase (crystalline or random state) offers a different amount of electrical
resistively which is used to distinguish between a "0" and and a "1".
RRAM (Resistive random-access memory) - This
non-volatile system saves data by altering the electrical resistance of a
material sandwiched between two electrodes. Current applied to the
electrodes are able to "switch" the ionic state of the material to conform to
one of two states of electrical resistance ... distinguishing between "0" and
"1".
MELRAM (Magnetoelectric Ram) - A group has found a way to manipulate the
spin of electrons to store data. These MELRAM cells are made up of two
magnetic alloys on top of each other that form a material whose spin orientation
reacts to mechanical stress. This composite material is set on top of a
piezoelectric substrate which provided the stress when an exterior voltage is
supplied.
Nano-RAM or
NRAM - This a
futuristic type of non-volatile memory which utilizes nanotechnology.
It could offer the non-volatility of flash memory, the speed of SRAM
(cache) memory, and the density (lots of memory in a small space) of DRAM
(capacitors & transistors). It offers low power consumption as well as
high durability. It works using carbon nanotubes that rest over an
electrode, which can be set in two possible positions - touching or separate (to
distinguish between logical states "1" and "0") ... depending if a voltage is
applied to the nano tube.
This
page gives a nice overview.
Here is a flash
video. This could be big!
RM (racetrack memory) stores bits of data as
magnetized regions on "racetracks" on nanowires. This is a nonvolatile
memory with no moving parts except electrons to read and write bits.
The bits themselves zoom along their racetrack, passing a read/write head at a
fixed location beside the wire. More
here.
ZRAM - This type of
memory could replace traditional cache memory (SRAM) because it uses only one
transistor (instead of 6) to hold a bit. The "Z" refers to the fact that
there is no capacitor (zero) to store the bit (which is used in DRAM). It
offers twice the space compression as DRAM and offers five times the density as
SRAM. It works using Silicon-on-Insulator transistors and the
"floating-body effect", where capacitance develops between the body of the
transistor and an insulating layer. I'm sorry but you will have to tell me
exactly how that works because I'm not a solid state engineer. If
interested, you can read more
here.
STT-RAM
(Spin-transfer torque RAM) - This memory exploits the "spin" on an electron that
can only have one of two orientations - up or down. As electrons move past
nano-magnets, they acquire the same spin as the magnets. This information
holds the bit values "0" and "1". The best part is this technology is
non-volatile and extremely fast so you may have instant-on computers in the
future. If interested,
this page has a great overview.
PCRAM (Phase change memory) - Certain substances (known as chalcogenide
glass) are able to switch between a crystalline and non-crystalline state by the
application of heat. This non-volatile form of memory may replace flash memory
some day because it is 500-1000 times faster and uses half the power.
FRAM (Ferroelectric
Random Access Memory) - In this type of non-volatile memory the alignment of a
molecule is achieved by an external electric field. Once the external field is
removed, the molecule retains its polarity to distinguish between "0" and "1".
MRAM
(Magneto-Resistive Random Access Memory) - It uses magnetic polarization rather
than an electrical charge to hold a data bit. In this type of
memory, two magnetic substances are separated by a non magnetic layer. One
of the magnetic layers remains fixed in polarity. However, the other layer
changes its magnetic orientation based on an applied external magnetic field and
thus, distinguishes the cells as either a "0" or a "1". Reading is
accomplished by passing a current through the cell. In one state it offers
little electrical resistance, but in the opposite state, the resistance changes
to a higher value. It only uses one transistor, is
nonvolatile, has unlimited endurance, no refreshing is required, and it is
better than Flash on write speed and durability. It was sampled to customers in
2006 so this is fairly new technology.
Working with Bits
- 1. Programmers often use another numbering system called hexadecimal (hex).
Briefly explain the base of this system, as well as the characters used to
express numbers. What is the reasoning behind this choice for counting?
What is the hex value of 2989 (base 10)?
Hexadecimal is a number system using 16 as a base.
It can make any number with the symbols 0-9 and A-F. We use base 10
because we have 10 fingers. By now you realize that computers use base 2
(binary). This is great for computers but bad for humans.
Programmers knew that they needed a numbering system based on some power of 2.
Hexadecimal seemed to be the logical choice because computers had registers of
16 bit lengths. With this system, you can identify the value in a 16 bit
register with just 4 symbols (which offers 2^16 or 65,536 possibilities).
You can enter 2989 into the windows calculator (in scientific mode) and easily
convert this to BAD in hexadecimal (a skill which will not be required on any test).
This page gives a nice
overview.
- 2. Calculate the disk space needed (in KB) to store a totally blank 24 bit
Bitmap picture whose dimensions (attributes) are 100 x 100 pixels.
Show the calculations. Would your answer change if the picture was
filled with art? Go to MS paint (or another readily available paint
program) and make a picture with these properties. What are the
approximate dimensions in inches? Save a totally blank image as a
GIF image. What is the file size? Calculate the compression ratio.
Fill the image with some home drawn art and save. Did the file size
change? Explain.
In a 24 bit Bitmap image, each pixel needs 24 bits to
store the color information. This is equal to 3 bytes. A 100x100
image requires 10,000 pixels. Just multiply to get 3 x 10,000 = 30,000
bytes = 30 kb. If you put colors into this image the size of the file
would not change but the values stored in each bit would. The size of this
image is very small .. only about 1¼" on a side
(you can get this in MS Paint by choosing image, attributes).
If you save the white bitmap image with a gif format (file, save as), the file
is reduced to 1 kb. This is a 30:1 compression. If you put art
into the picture, the file size will increase (depending on what you put in
and how much contrast it contains). However, the file size will very
likely be much less than the 30 kb size of the bitmap image.
-
3. Show how you can construct an XNOR
gate using any combination of the gates introduced in this unit.
As an aid, I've included the truth table for
this gate:
The XNOR table
| Input A |
Input B |
Output Value |
| 0 |
0 |
1 |
| 1 |
0 |
0 |
| 0 |
1 |
0 |
| 1 |
1 |
1 |
Making the XNOR gate is actually quite easy ... just look at the
XOR gate truth table and turn everything around. To do this, just add a
NOT gate at the end (see image below). If you want to get fancy, I've
indicated two other versions below that do the same thing.
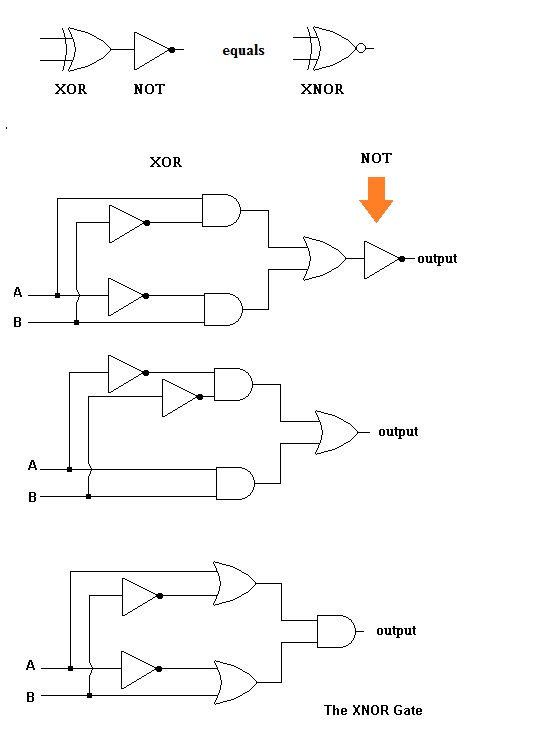
Three ways to make the XNOR Gate
- 4. Trace the following values through either full adder, showing clearly the
values at each gate's input and output.
|
A |
B |
CI (carry in) |
CO (carry over) |
Output |
|
1 |
0 |
0 |
0 |
1 |
As an aid, you can print a copy of the full adder
here (or improved adder
here)
Please make sure you can trace values through this (or any
other) system of gates just like I've shown below. You may have to do the
same on the test. The key is to apply the truth tables for each gate
properly. If you want some more practice, trace some input values through
the XNOR gates printed above.
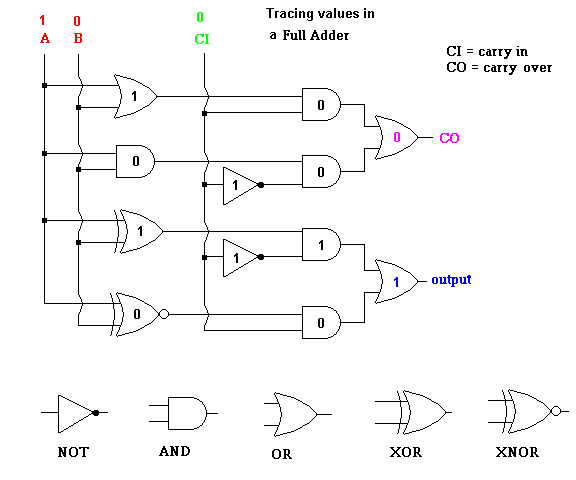
The Internet
- 1. Compare DSL, and cable Internet access in terms of speed, cost
and availability. List some advantages and disadvantages of each choice.
How you connect to the Internet is mainly a matter of
cost, availability, reliability, tech support, and speed. As you have
read in the class material, there are many ways to gain Internet access but we
will limit this topic to DSL, and cable. There is no magic
formula to help you make an correct decision but there are things you should
know to help you make an informed decision.
Cable: Download Speed is typically 1-100 Mbps and you get this through
your local cable company. The actual speed depends on how many people in
your neighborhood are accessing the service at the same time (as well as other
factors such as artificial caps imposed by your provider). However, this
is also the costliest choice. For example, the normal charge for Time
Warner is $35-$65 /month (depending on download speed you pick
... also they have a lower introductory
offer).
DSL: The
actual speed varies greatly between households, depending on the type of
copper wiring used, type of computer and router but mostly how far you live
from the central hub. You may be able to obtain speeds up to 25 Mbps. It is best if you call your provider to estimate
the actual speed you can expect. Each DSL provider also offers several
plans with download times that vary. You typically obtain access through
your local phone company (since the signal comes through phone wires ... at a
frequency with will also let you make phone calls). You can expect to
pay somewhere between $15-$30/month. Speed for DSL is slowly catching up
with cable thanks to two technologies - bonding and vectoring. Bonding
speeds things up by using multiple phone lines. Vectoring (still in
development) compensates for the noise and interference normally found in
phone lines. Vectoring may provide speeds around 100 Mbps (wow).
BTW: Anyone remember Dialup? Squealing modems and watching
the paint dry as something came in!
-
If interested, here are some interesting articles:
DSL vs. Cable
Speed Comparison
-
-
2. If you live in a very remote location with no phone
service or cable access, is it still possible for you to access the Internet?
If so, who provides this service and how much will it cost?
Air
cards (on laptop computers) and tethering to a cell phone are ways to access
the Internet. However, both need to be areas of local service to work. However, satellite
Internet service providers only ask you to have
a clear view of the southern sky.
Exede,
DishNET, and
HughesNet are some providers of remote Internet.
Plans are based on access speeds and download limits but you can get your foot
in the door for about $60/month
3. What is the difference between a virus, worm, spyware, and a Trojan horse?
Give examples of the inconvenience each can cause.
We all have to be careful to keep our computers systems isolated and the
information on it private. When you go online shopping, much of your
activity is stored in cookies (a small file stored on your computer).
This way, the next time you go to amazon.com, they know who you are and what
you have done on their sight. For the most part, cookies are harmless.
Somewhat more intrusive is
spyware. This
is a program designed to do any of the following: track personal
information, display unwanted pop-ups, add icons to your desktop, or change
initial settings in your browser. This code often enters your system
when you download and install cheap or free software. You can even pick
this stuff up just by visiting the wrong web site ... called a "drive by".
The way around this is to make sure your security software (virus / firewall)
program handles spyware as well and stay away from web sites that are
"objectionable".
A virus is a malicious program that attaches itself to an executable file.
It behaves much like a real virus in that it tries to copy itself in
hopes of infecting other systems. To activate it, a person needs to open it.
One common way a virus spreads is via attachments in email. When you
open the file, it infects your computer. This can be a playful prank to
downright nasty programs meant to damage your system or files. To
replicate itself, it can look up your email address book and send copies of
itself to all your friends.
A worm is much like a virus but does not require intervention by a
person to replicate itself. For example, it can cripple all computers in
a network by exploiting security holes.
A Trojan horse is a program (software) that is intended to do one thing but
ends up doing something unintended. A Trojan horse does not replicate.
How ironic. Just as I was writing this, I launched a Trojan in a file
mgrs.exe. How it ended up on my computer is still a mystery. My
firewall caught this program asking for permission to the Internet. Like
an idiot, I let it through (thinking it was for windows messenger ... as the
perpetrator intended). A few $$$ later, I eradicated this dangerous "malware"
program. Here is a
review of some software you can purchase ... just in case. PS: This
was NOT caught by my antivirus program. I'm very fortunate I ceased all
Internet activity as soon as I noticed new icons appearing on my desktop.
If interested, click
here to read more.
4. Give one reason why your IP address probably changes every time you
access the Internet (called dynamic IP address)? Hint: It is partly to solve
a problem the original developers of IP addresses didn't envision.
Quite simply, they are running out. The format range is from
0:0:0:0 to 256:256:256:256 which gives just over 4 billion unique
possibilities. A new format called IPv6 will solve this problem because
it is virtually limitless.
- What is spam? List things you should do to avoid it.
Spam is unsolicited bulk email. There have been
many attempts to block spam and each time the spammers have found a way around
the system. For example, your ISP can go to
spamhouse.org to get a
list of IP addresses of known spammers and block them. All they do is
obtain another IP address and anyone who picks up the old IP automatically
becomes blacklisted. They can hijack your machine and make it a "spam
zombie"
so it looks like the spam came from YOUR machine.
Rule #1 - Avoid printing your email address on web pages or in chats.
If you must, disguise it like johndoe AT someplace DOT com.
Your email program will likely have a spam filter. If too much gets
through, move it to a higher setting. However, this may block some legitimate
emails. You can also set up "rules" to handle email. For example,
my email program sends email with common spam phrases directly to the trash.
-
- Besides a firewall, spam protection, and virus protection, what other
security steps should you take to avoid problems from Internet intruders?
If you have a wireless network, make sure your router
only gives
access encrypted with a key. WEP is an encryption tool on wireless networks designed
to prevent introducers. However, all you have to do is ask the folks at
TJX just how secure that system is. The short answer - not very.
A much better security standard is called WPA. Use that standard
if you have the option. As an added layer of security, have your router
only grant access to known computers on your network. Each machine has a
unique MAC address (at the command prompt type ipconfig /all to find
it). It is possible to have your router filter your home network to only
include machines you want. This is a sure-fire way to protect yourself
from intruders.
A common practice (called
phishing)
is an attempt to trick you into giving your personal information away.
It does this by mimicking an "official looking" email from a place you may do
business. You may be asked to give you social security number, credit
card number, bank account and pin number, etc. DON'T DO IT!
If you shop online, make sure your browser is up-to-date and you send
sensitive information over an encrypted site (a tiny lock appears). The
way this works is the site you go to sends you an encryption key and after
that, all information is scrambled. If you have a hard wired Internet
connection it is virtually secured. Even if you send this over wireless
you can feel secure because any hacker would first have to intercept the
encryption key and then use it. Virtually impossible. Make sure
you have a secure wireless network at home.
Here is a great article that offers 10 tips to wireless security.
-
- HTTP stands for hypertext transfer protocol.
It is the standard way most web pages are handled over the Internet, ... but
not the only way. Give one example of a different format for
transferring data. What are the advantages? Give a brief overview
and offer a way we can experience it first hand.
Perhaps I'm dating myself but I remember the Internet
before there were any web pages (http://). Back then, you downloaded
from a remote computer using FTP (file transfer protocol). Do you
remember gopher, and telnet? Your email is now handled by a different
format: SMTP (Simple Mail Transfer Protocol).
But let's not make this a history lesson,
we should look to the future and concentrate on new innovations for the next
generation of Internet users
HTTPS:// (Hypertext Transfer Protocol over Secure Socket Layer)
is now commonly used as a security option. It is an attempt to encrypt
any information you send or receive from that site. Make sure your next
online shopping spree is done securely. Look for a small closed lock
icon somewhere on the page and look for the HTTPS in the address
bar.
RTSP (Real-Time Streaming Protocol) is used to stream video and voice
over the internet. It is used in Skype and QuickTime, for example.
ICMP (Internet Control Message Protocol) is used
to "ping" a specific server ... basically to determine the speed of the
connectivity between you and them. It also can be used to trace the
router paths to determine hop counts and other transfer information that can
be used to detail where your data is going to any specific point.
-
XML (EXtensible Markup Language) is a protocol
designed to transfer date over the Internet. It is also much more "human
friendly" to write in than HTML. If interested, click
here to read more.
-
- UDP (User Datagram Protocol) is another type
of data transfer. We most often see it in streaming music and video, as it is
designed specifically for fast, but unreliable, non-secure data transfer.
Meaning, you get most of what is sent, but not everything, and not all the
time. That's okay so long as the data being sent is trivial i.e. not your
savings transfer to a bank.
AJAX (Asynchronous JavaScript And XML) is a
Google initiative that makes greater use of JavaScript over the Internet.
Specifically, it allows you to download tiny bits of information from a server
rather than a whole page at once. Just go to
Yahoo
maps and see how you can move the map around
without refreshing the entire screen.
Weighting a Fish - Here are a couple of ideas (all from students) ....
- A simple scale ... which is like a lever. If 10 pounds on the other
side balances the scale, your fish weighs 10 pounds too. Daaa!
Likewise, you could use a single pulley and
string with some weights. You hang the pulley, then you hang the fish on side,
and you slowly add weights to the other side till the fish and the weights are
equal. Then you will know actually how much the fish weighs.
- How about placing the fish on a piezoelectric crystal? The more it weighs,
the more stress on the crystal .. the greater the voltage ... which is picked
up on a digital display.
- Let our fish dangle from a piezo-resistive wire. That is, as the
stress in the wire changes, so does the electrical resistance in the wire ...
which is picked up by a microchip.
- Have a board of cork free
floating atop water and set the fish on this board. The water level will rise as the
water is displaced and can be measured by markers on the side of the tray of
water that the cork board is set in.
This would only give you the volume of displaced water
but it is a very good start (and worth full credit here). Have you heard of
Archimedes' principle? It says that the weight of the displaced water is
equal to the "buoyant force". If you want to weigh a boat, you could put
it in a brim full bath tub (the tub might have to be pretty big) and let water
overflow. Now weigh the overflow water and you have weighed the boat.
This is essentially what you have done here – only don’t just measure the
displacement height … find the weight of the displaced water instead.
Remember that the number you get is the fish plus the cork slab so take that
into account by subtracting it in the end to get the fish weight alone.
Jim
- Get a transparent cylindrical container of known diameter. Fill it about
half way and mark the level of the water. Drop the fish into the water and
then measure how much the water level has moved up from the mark. From this
you can calculate the volume of water displaced (at 8 lbs/gal) and you'd know
how much the fish weighs.
This is
assuming they both have the same density. For example, if the fish were made
of lead, it wouldn't work without a correction factor. However, I think you
can assume the fish is about the same density as water.
Jim
- I know we weren't suppose to use
the Internet but I found this interesting. I found that you could find the
weight of a fish by applying simple math by measuring the fish from tip of its
nose to fork of the tail then around the fish in the front of the pectoral
fins (girth). Now if you take the girth measurement (the circumference
around the fish taken in the front of the pectoral fins measured in inches) and square it, then multiply this
by the length measurement (again in inches) and divide the product by 800 you will come out with
the weight of the fish in pounds.
Okay maybe it isn't simple math but it does work.
Way harder and more complicated then the scale, but it works.
- OK, HOW ABOUT THIS. YOU WEIGHT
YOURSELF ON A WEIGHING SCALE, THEN WEIGHT YOURSELF WHILE HOLDING THE FISH.
AFTERWARDS, JUST SUBTRACT THE AMOUNT YOU WEIGHED ALONE, TO THE AMOUNT YOU
WEIGHED WITH THE FISH. I'M PRETTY SURE THIS WOULD WORK ACCURATELY.
OK .. a bit lame but you know, this is exactly how I ended up weighing my bike
and a bike rack (to see if I've exceeded a weight limit) ... so I'll take it.
Jim
- Get a spring and set it on a desk
then get a board and put this fish on top of the "spring board". The spring
will compress more or less depending upon the weight of the fish. (In
your example you relied on spring expansion, not compression).
One must be sure the spring is not fully compressed or you won't get a true
reading.
- In a capacitor, if the plates change their distance with respect to each
other then the voltage changes as well. OK, so you could somehow hang your
fish from a string but put a capacitor in between so the weight of the fish
could pull the plates apart slightly. The heavier the fish, the more the
plates would be pulled apart. I suppose you would have to calibrate this
with known weights first but after that it should give an accurate reading.
Super answer xxxx. Too bad you didn't think of this earlier because, in
fact, this has already been thought of. It is called a capacitive
sensor. One plate is held fixed and the applied force is able to move
the other plate (just as you said). Good job!
Jim
- This might make the fish mad but you could apply a known force to your
fish and measure the acceleration you get as a result. Since
Newton's laws would apply here, you could derive the mass of the fish from the
equation F = ma. You would know F and "a", then solve for "m" which is
the mass of the fish.
I can see you took a physics class. You found a great solution (and
don't worry, the fish is already dead). Now I'll bet you didn't know
that this is exactly how they "weight" astronauts in space. Your
bathroom scale would be useless in orbit so they literally shake the poor
space traveler in a chair. Since they still have inertia, the amount of
resistance their bodies offer to the apparatus, the more mass they have.
This chair is calibrated on the surface of the earth so you can match the
machine results (which works anywhere) with their surface weight.
Jim
- I'm not sure if you this would work but you could make an electromagnet
and then keep adding more current which would make the magnetic field
stronger. Now you have to keep the hook in the fishes mouth because you
would need something that would hold the fish to the magnet. Now keep
adding current until it's enough to support the weight of the fish (plus the
hook). Once it does, you should be able to read the current and
calculate the weight.
Yes, but it would be easier to just celebrate the apparatus with known weights
first and then your idea is perfect. You may need something more than
just a small metal hook but that is all I have to add.
Jim
- My fish scale would start with a rod that lends itself to bending without
breaking, something like those rods that are used in a bowflex machine. The
rod would be held horizontally and the fish would be hung from the end of the
rod. The weight of the fish would cause bending of the rod. Heavier fish would
obviously cause more bending and lighter fish would cause less bending.
The rod would have a top and a bottom. A piezoresistive material would be
built into the center lower part of the rod, at the point where a bending
force would cause a compression of the material that makes up the rod. Battery
supplied current would be sent through the piezoresistive material just before
weighing. (the device would be turned on.) As the fish was hung from the
cable, the rod would bend causing pressure to be applied to the piezoresistive
material. The electrical resistance of the piezoresistive material would
change as pressure was applied to it. The changes in the current (amperage)
would be detected by the computer chip in the electronics of the scale and
should be in proportion to the amount of bending. The weight of the
fish would be displayed on a digital display.
Super duper answer xxxxxxx
Normally I'd tell you to go and patient but guess what ... already done
(although maybe not for weighing fish). The rod actually has two
piezoelectric crystals (maybe for accuracy) ... one at the top where the rod
is pulled apart (tension) and one at the bottom (where it gets compressed).
A piezoresistive crystal could be used but that is called an "active"
sensor .. meaning an outside power source is required. If you just use a
piezoelectric crystal (which makes its own power .. which is called a passive
sensor) I guess it is a bit cheaper??? But there is even more to your
post that I need to expand on. You say the degree of deflection is an
indicator of weight. Correct! In the case of a spring, the
distortion is caused by a force "in line" with the spring (something related
to stress) and the distortion is called
strain. In the
case of an applied torque, it is called a shear stress and the resulting
deformation is called a
shear strain and you
are 100% correct. Within the elastic limit, the degree of bend is
proportional to the weight of the fish.
Jim
